Tokenization
Tokenization makes sensitive information safe by swapping it with non-sensitive data called "tokens." These tokens can be used in a database or internal system without exposing sensitive information.
What sets tokenization apart is that the tokenized data is indecipherable and cannot be reversed. This means there's no direct link between the token and the original data. You can't convert tokens back into the original sensitive information without specific additional data stored separately. So, even if there's a security breach in a tokenized system, the original sensitive data remains safe and isn't compromised.
What is a token?
A token is a piece of data that stands in for another, more valuable information. Tokens have virtually no value on their own, and they are only useful because they represent something valuable, such as a credit card primary account number (PAN). The tokens are generated using mathematical algorithms and can't be reversed.
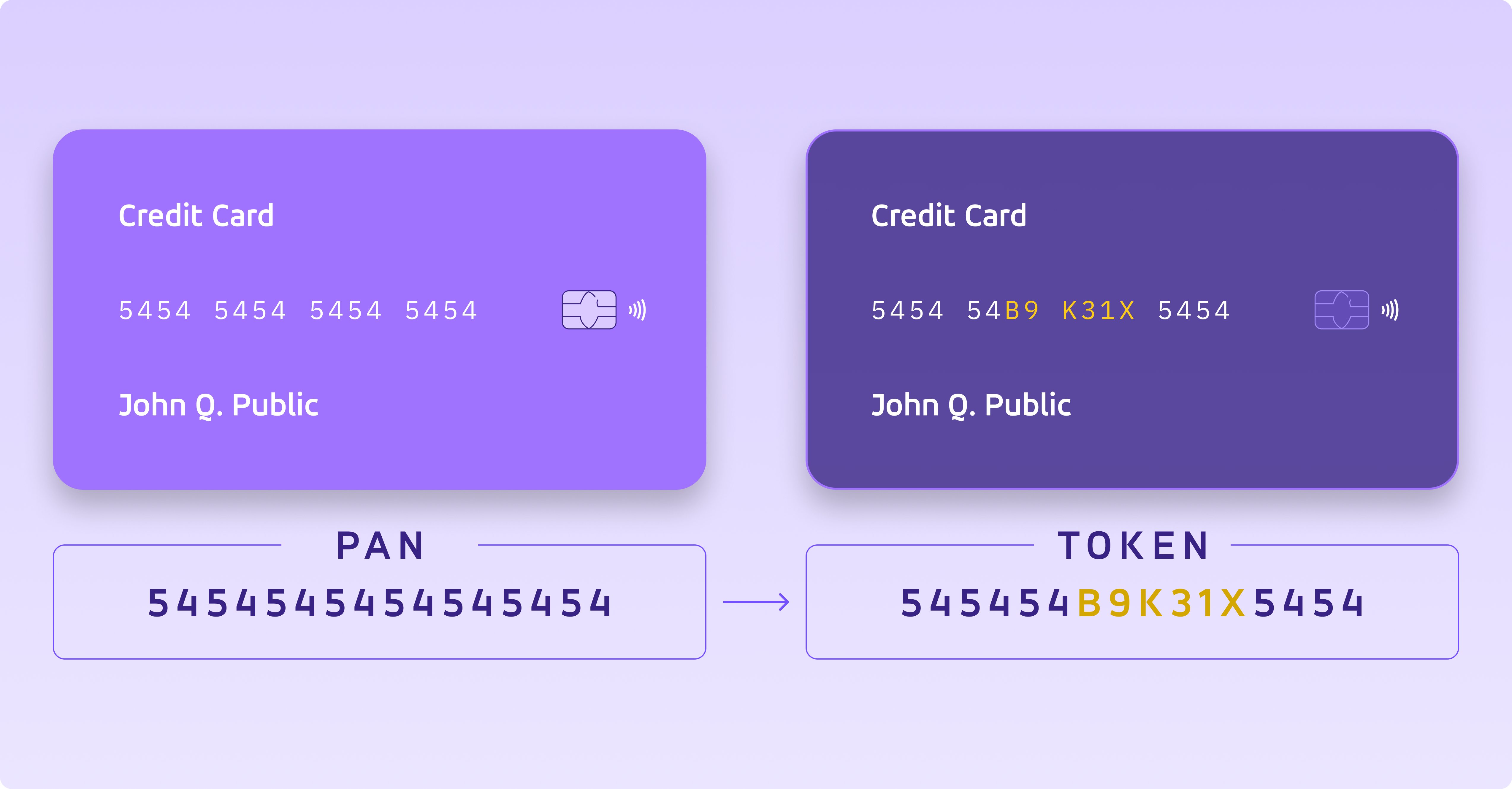
Even though tokens may seem unrelated, they still keep certain aspects of the original data, like length or format, so that they can be used in regular business operations without any issues. The original sensitive data is stored securely outside the organization's internal systems.
How does tokenization work?
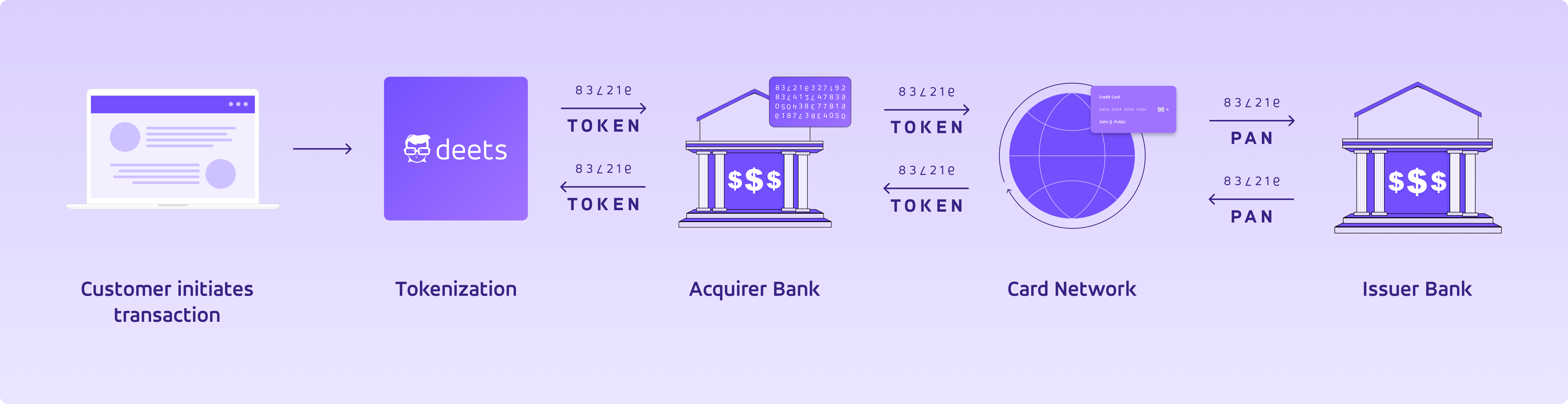
Tokenization swaps the sensitive Credit card data with a randomly generated token to safely access, pass, transmit, and retrieve customer credit card information. The flux below presents a transaction with credit card tokenization:
Where:
- Cardholders initiate a transaction and enter their sensitive credit card data.
- Deets captures and sends the information to the merchant acquirer bank as a token.
- The Acquirer Bank transmits the token to the credit card networks for validation and authorization.
- Once authorized, the data is sent to the Card's issuer bank.
- The issuer bank authorizes or declines the transaction.
- When authorized by the bank, a unique token is returned to the merchant for current and future transactions.
This process is done behind the scenes, so customers and cardholders do not see or take part in it.
Tokenization vs Encryption
Tokenization aims to protect sensitive data while preserving its business utility. This differs from encryption, where sensitive data is modified and stored with methods that do not allow its continued use for business purposes. Additionally, encrypted numbers can be decrypted with the appropriate key. Tokens, however, cannot be reversed because there is no significant mathematical relationship between the token and its original number.